In the rapidly evolving digital landscape, Application Programming Interfaces (APIs) have become the cornerstone of modern software development. APIs enable seamless communication between different software systems, allowing them to share data and functionality. From e-commerce and social media platforms to mobile applications and cloud services, APIs power the interconnected digital world we live in. However, the increased reliance on APIs has also raised concerns about security vulnerabilities and the potential risks they pose to the digital ecosystem. This article delves into how important API security is for protecting the reliability, privacy, and accessibility of digital ecosystems.
APIs are like a set of rules and tools that let different software applications talk to each other. They define how requests and responses should be structured, enabling developers to integrate third-party services, extend functionality, and create innovative applications. APIs can be used to access a variety of resources, such as databases, hardware components, and external services.
The digital ecosystem encompasses a vast network of interconnected devices, applications, users, and data sources. APIs enable these components to work together seamlessly, facilitating data sharing, automation, and improved user experiences. For instance, a weather application can use an API to fetch real-time weather data from a remote server, enhancing the app’s accuracy and relevance.

While APIs provide numerous benefits, they also introduce potential security vulnerabilities that malicious actors can exploit. The following are some key reasons why API security is paramount in safeguarding the digital ecosystem:
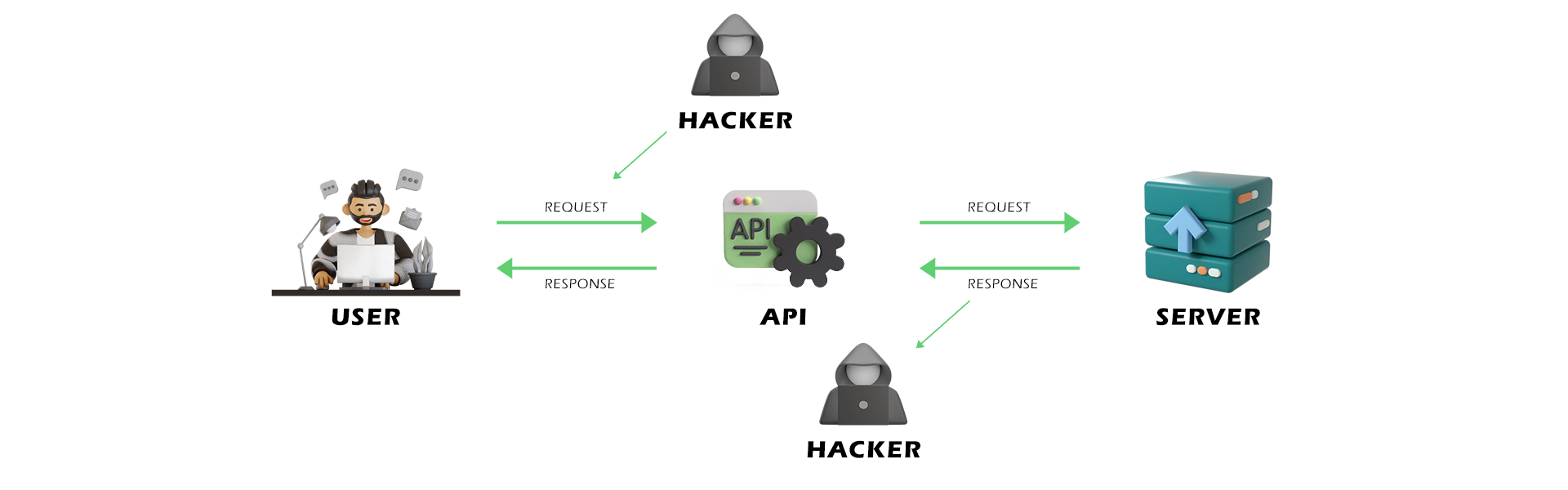
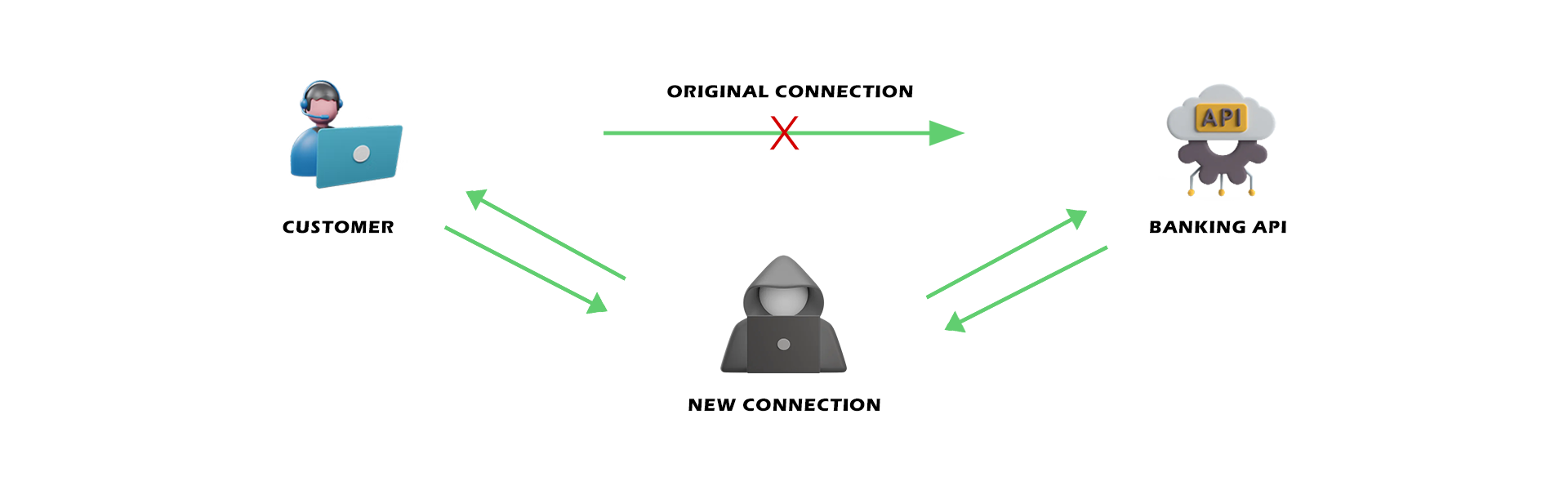 Insecure Dependencies: APIs often rely on third-party libraries and components. If these dependencies have security vulnerabilities, they can be exploited to compromise the API.
Insecure Dependencies: APIs often rely on third-party libraries and components. If these dependencies have security vulnerabilities, they can be exploited to compromise the API.
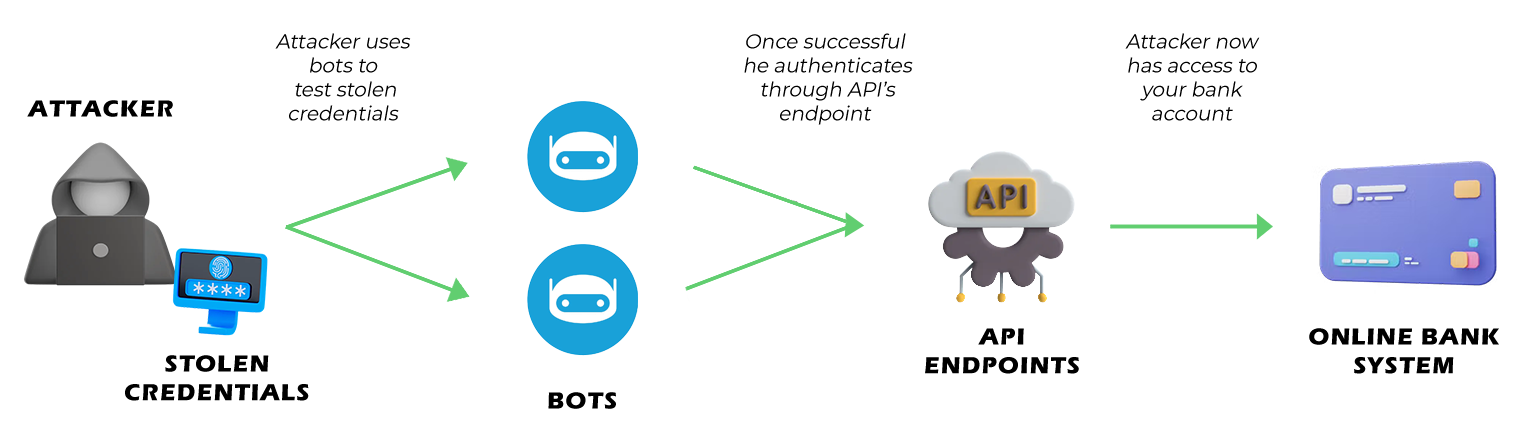
To safeguard digital ecosystems, organizations must adopt comprehensive API security measures:

A zero-day hack on Twitter in August 2022 affected at least 5 million users, with the potential to impact over 20 million. Twitter fixed the vulnerability in January 2022, but a recent report by Bleeping Computer reveals that a database containing non-public information of more than 5 million users has been freely shared on a breached data marketplace forum. Additionally, another database potentially containing 17 million records was created using the same vulnerability. While most of the data includes publicly known information like usernames, it also includes private data such as phone numbers and email addresses. This breach highlights the urgency of securing online platforms and the risks associated with API vulnerabilities.
The data appears to have been acquired through an API vulnerability, initially disclosed by a hacker on HackerOne who received a $5,000 reward from Twitter. APIs are crucial for internet traffic but are prone to security issues like authentication, resource limitations, and misconfigurations, as noted by Ed Williams, director of SpiderLabs at Trustwave. Recent breaches emphasize the risk of such issues leading to substantial data leaks.
APIs play a pivotal role in today’s interconnected digital ecosystems, enabling seamless communication and innovation. However, the potential security risks associated with APIs cannot be ignored. To ensure the integrity, confidentiality, and availability of digital ecosystems, organizations must prioritize API security measures. We at Ethic IT implement strong authentication, authorization controls, encryption, and regular security assessments, businesses can build trust with users, protect sensitive data, and mitigate the risks posed by malicious actors. As the digital landscape continues to evolve, we provide best robust API security which remain a cornerstone of a resilient and secure digital ecosystem.

Consult with Ethic-IT for a free Proof of Concept (POC)
Email us: sales@ethic-it.com
Call us: 045687393 / +97145807199
© 2024 Ethic IT, All Rights Reserved | Legal Notice